Pre requirements
- MakeCert is a MS certificate creation tool which generates self-singed certificates for testing purpose. We will need the makecert.exe to generate our self-singed certificates. (More Information’s could be found here https://msdn.microsoft.com/library/windows/desktop/aa386968.aspx)
Test Environment
Our Test environment has two servers without a domain that mean we will use a basic Workgroup setup for this HowTo (if the two servers will be part of the domain a replica with SSL setup you could leave out Step 5).
Our setup looks like the following:
- Hyper-V Host 1 [VMH01] (Primary)
- Hyper-V Host 2 [VMH02] (Secondary)
1. Creation of the root certificate
In the first step we will create a root certificate that both servers can use.
Run the following command on our primary Host VMH01 to create a self-signed root certificate.
makecert -pe -n "cn=TestHyperVRootCA" -ss root -sr localmachine -sky signature -r "TestHyperVRootCA.cer"
The command will install in the certificate into the root store of the local machine and saves the file locally.
2. Creation of Host certificates singed with our root certificate
Now we will create our Hyper-V Hosts (VMH01, VHM02) certificates and signing them with our previously created root certificate.
Please Replace with FQDN of Hyper-V Hosts machines e.g. VMH01, VMH02.
Run the following command to create a certificate signed by root certificate for the Host: VMH01:
makecert -pe -n "cn=<FQDN>" -ss my -sr localmachine -sky exchange -eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in "TestHyperVRootCA" -is root -ir localmachine -sp "Microsoft RSA SChannel Cryptographic Provider" -sy 12 VMH01Cert.cer
Run the following command to create a certificate signed by root certificate for the Host: VMH02:
makecert -pe -n "cn=<FQDN>" -ss my -sr localmachine -sky exchange -eku 1.3.6.1.5.5.7.3.1,1.3.6.1.5.5.7.3.2 -in "TestHyperVRootCA" -is root -ir localmachine -sp "Microsoft RSA SChannel Cryptographic Provider" -sy 12 VMH02Cert.cer
The previously executed commands will install two certificates into the Personal store of the local machine and saves the file locally. The created certificates can be used for both Client & Server authentications.
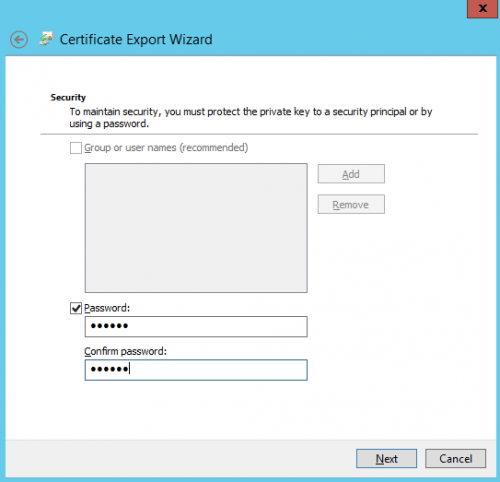
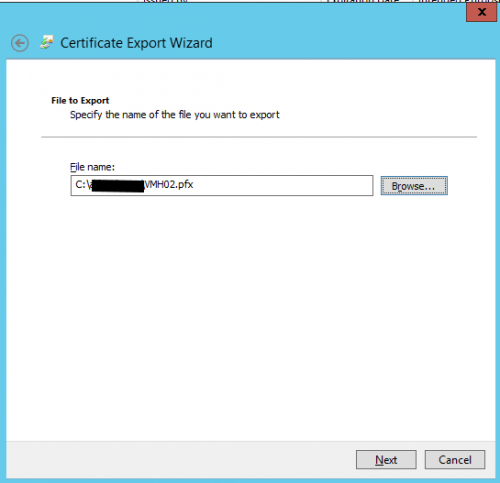
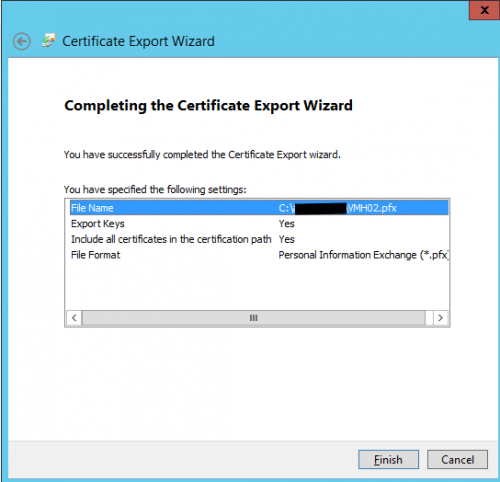
3. Export of our certificates to the secondary Host
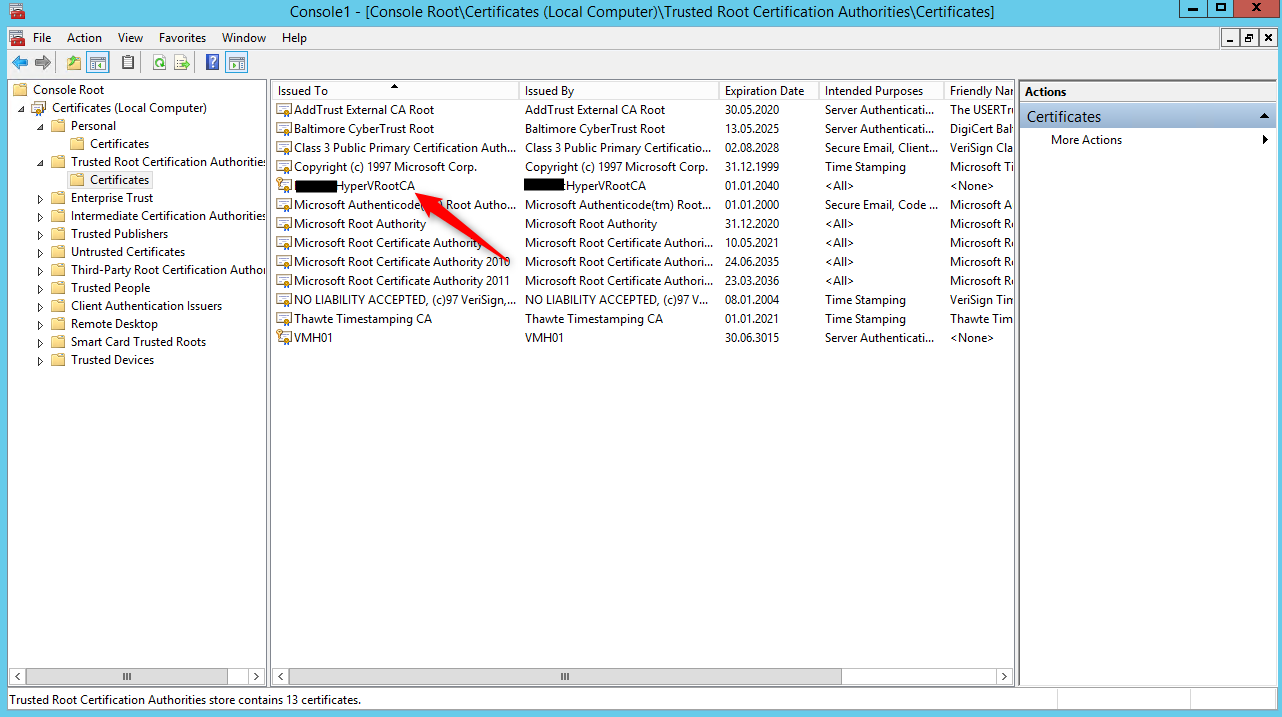
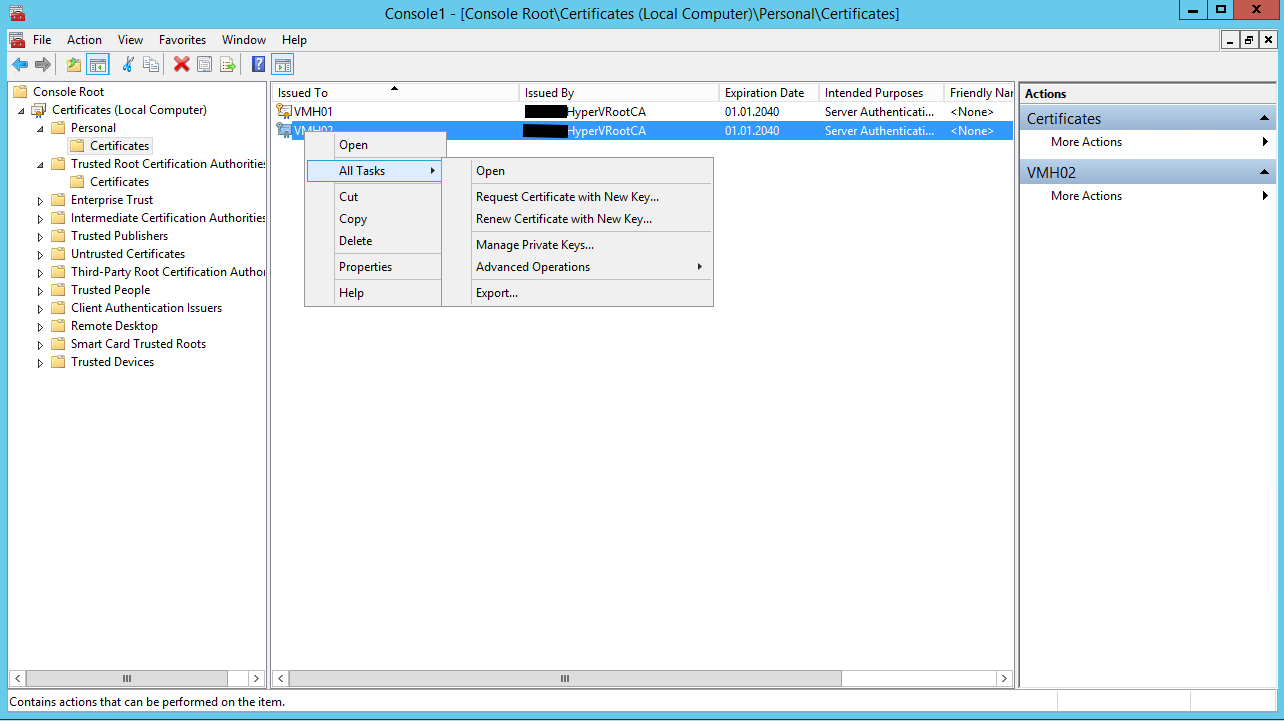
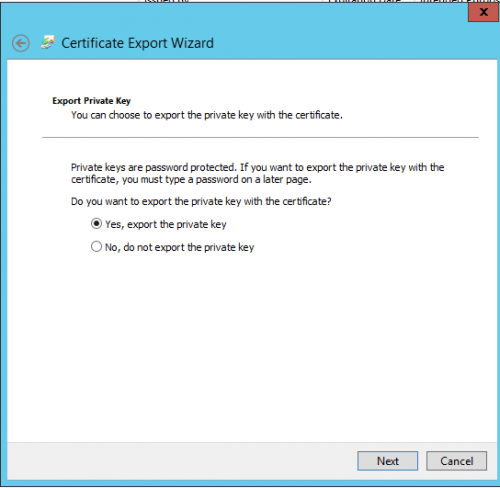
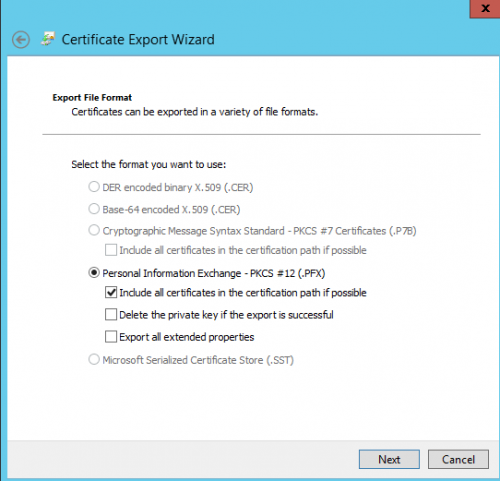
Open the mmc certificate Snap-In (Local Computer) on our primary Host VMH01 and export the certificate (with Private Key) that has been generated for VMH02 (see screens below).
4. Setup certificates on secondary Host VMH02
Copy TestHyperVRootCA.cer and the above exported certificate (VMH02.pfx) to our secondary Host VMH02.
Run the following command from an elevated prompt on the secondary Host to import the self-singed root certificate:
certutil -addstore -f Root "TestHyperVRootCA.cer"
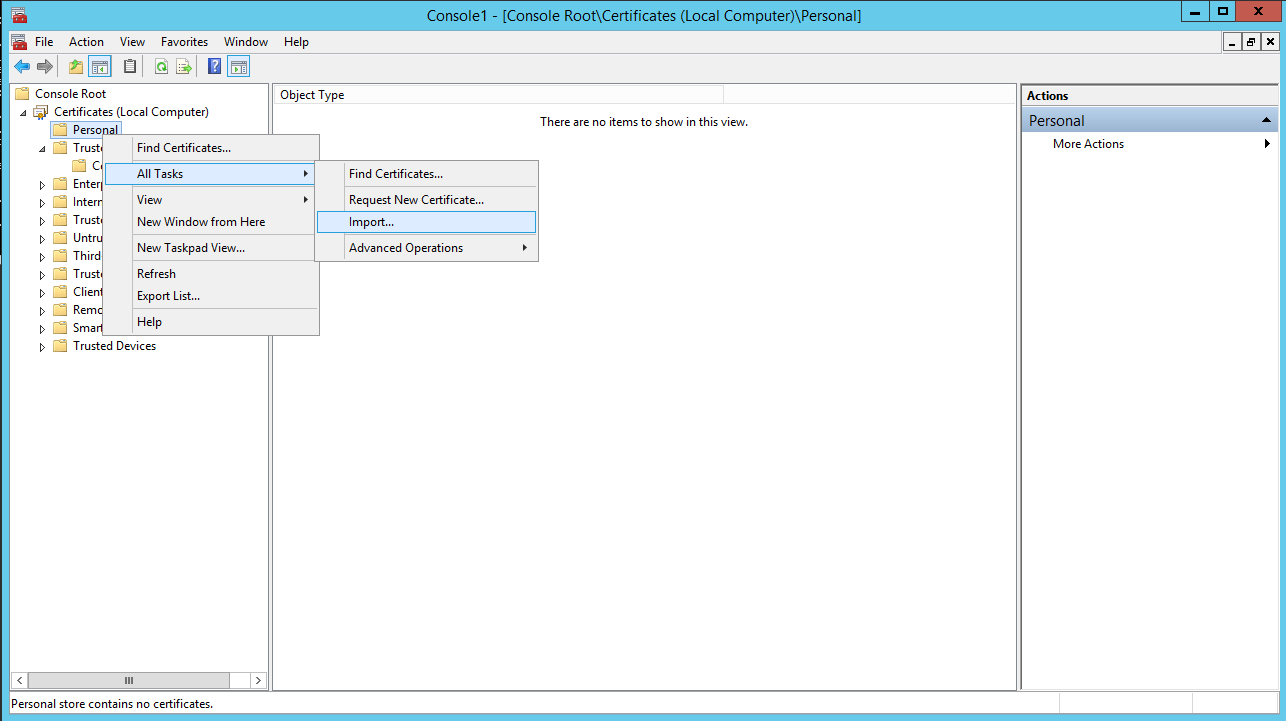
Open the mmc certificate Snap-In (Local Computer) on our secondary Host VMH02 and import the certificate (VMH02.pfx) in the Personal store of the server (see screen below).
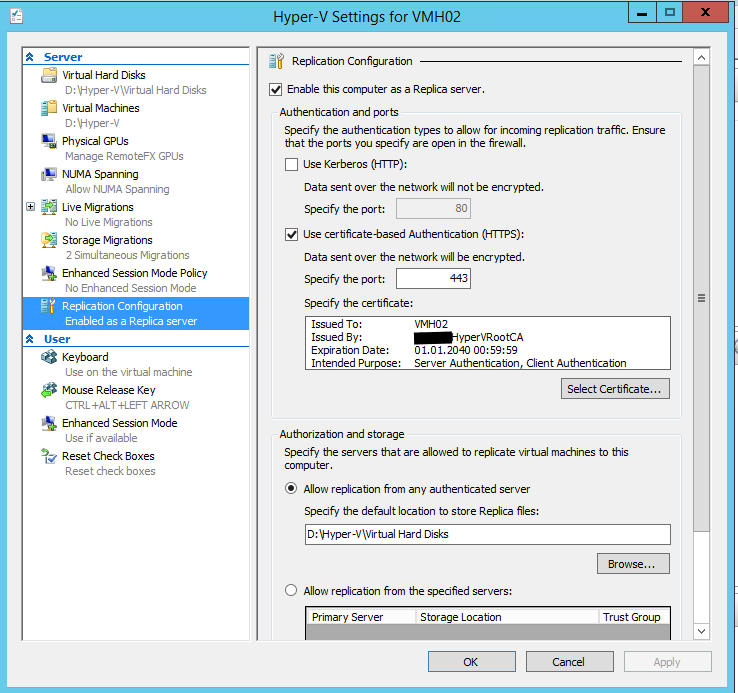
5. Revocation of self-signed certificates
Please note by default a certificate revocation check is mandatory and self-signed certificates don’t support revocation checks on Windows Server 2012.
Please modify the registry key on both machines (primary and secondary) to disable the check:
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\Replication\
Set the Value for DisableCertRevocationCheck to 1 (disabled).
Keep in mind that maybe a reboot of the System is required!
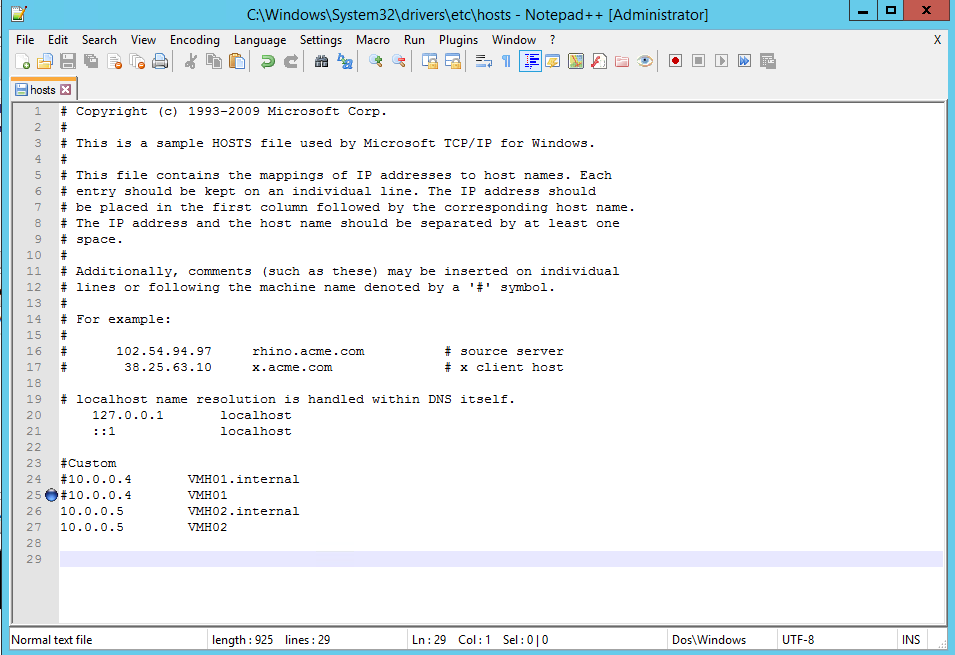
5. Publicize servers in the workgroup network via windows hosts
To ensure that our servers find each other in a non-domains setup, we need to make some small changes hosts file of the respective hosts. This will be necessary cause Replica only work with FQDN entries.
To ensure that our servers could find each other in a non-domain setup, we need to make some small modifications on the server’s hosts because replica will only work with FQDN entries.